Some Known Factual Statements About S3 Cloud Backup
Wiki Article
The 7-Minute Rule for S3 Cloud Backup
Table of ContentsGetting My Aws S3 Backup To WorkWhat Does Ec2 Backup Do?The Definitive Guide to S3 Cloud BackupAll About Ec2 Backup
You can make use of firewalls to ensure that just accredited customers are enabled to gain access to or transfer data. These measures are generally made use of as part of an identity and access management (IAM) solution and also in mix with role-based accessibility controls (RBAC).File encryption protects your information from unauthorized access also if data is swiped by making it unreadable. Endpoint defense software generally enables you to check your network boundary and to filter traffic as required.
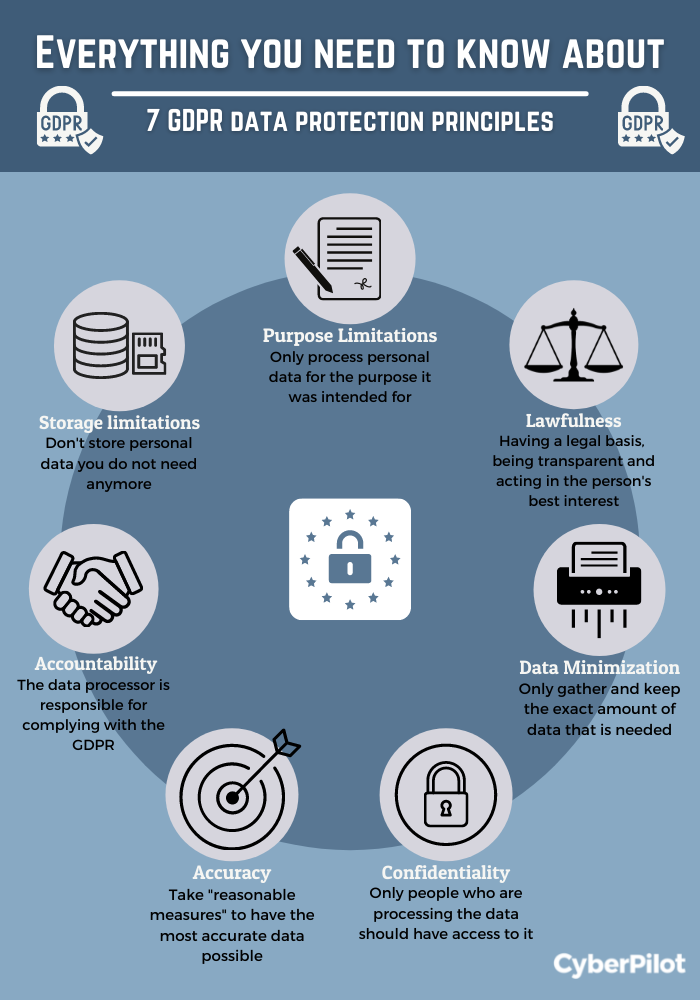
This can be done after information is refined and examined or occasionally when data is no longer appropriate. Eliminating unneeded information is a requirement of numerous compliance policies, such as GDPR.

Aws Backup for Dummies

Reducing your data collection can additionally assist you save on transmission capacity as well as storage space. These systems utilize third-party data to validate individuals and remove the requirement to store or transfer individual data to your systems - https://www.sudobookmarks.com/author/clumi0/.
Showing this, GDPR has made user authorization a crucial aspect of information use as well as collection. You can be certain to include individuals as well as their consent in your processes deliberately privacy problems right into your interfaces. ransomware protection. Having clear individual notifications describing when information is collected and why. You should likewise consist of alternatives for users to customize or opt-out of information collection.
Data portability is a crucial need for several modern IT organizations. It implies the capability to relocate information in between various settings and also software applications. Very typically, information mobility indicates the capability to move information in between on-premises information facilities and also the general public cloud, and also in between various cloud service providers. Data portability likewise has legal implicationswhen data is kept in various nations, it goes through various legislations as well as guidelines.
Getting My Ec2 Backup To Work
This makes it tough to move information from one cloud to an additional, and develops supplier lock in. Progressively, companies are searching for standard means of storing as well as handling information, to make it portable across clouds. Smart phone defense describes steps created to protect sensitive info kept on laptops, mobile phones, tablet computers, wearables and also various other mobile tools.
In the modern-day IT setting, this is a vital element of network protection. There are lots of mobile information protection devices, designed to protect mobile phones and also information by determining dangers, developing back-ups, and also preventing threats on the endpoint from reaching the company network. IT image source team usage mobile information security software program to make it possible for protected mobile accessibility to networks and also systems.
Ransomware is a sort of malware that secures user data and demands a ransom money in order to launch it. Brand-new types of ransomware send the data to assaulters prior to encrypting it, enabling the opponents to obtain the company, endangering to make its sensitive information public. Backups are an effective defense versus ransomwareif an organization has a recent duplicate of its information, it can restore it and reclaim accessibility to the data.
Not known Details About Protection Against Ransomware
At this stage ransomware can infect any kind of connected system, consisting of back-ups. RTO. When ransomware spreads to back-ups, it is "game over" for information protection techniques, due to the fact that it becomes impossible to recover the encrypted information. There are multiple methods for preventing ransomware as well as in certain, stopping it from infecting backups: The most basic strategy is to use the old 3-2-1 backup guideline, keeping 3 duplicates of the information on 2 storage space media, among which is off properties.Storage suppliers are using immutable storage space, which ensures that information can not be modified after it is saved (https://bubbl.us/NzM3NTA0Ny81MTA4NTgzL2QzZjUzY2Y1ODc2MWYwY2ZiNGExNzUzNzBjNDhiNGEw@X). Big companies have numerous datasets stored in various places, and also numerous of them might duplicate information between them.
It is no usage safeguarding a dataset as well as guaranteeing it is compliant, when the information is duplicated in an additional unknown location. CDM is a sort of solution that finds duplicate information and assists handle it, comparing comparable information and permitting administrators to delete unused duplicates. Calamity recovery as a solution (DRaa, S) is a managed service that offers an organization a cloud-based remote catastrophe healing website.
With DRaa, S, any size company can reproduce its local systems to the cloud, as well as quickly recover procedures in case of a catastrophe. DRaa, S solutions utilize public cloud infrastructure, making it possible to keep numerous duplicates of infrastructure and data throughout several geographical places, to raise resiliency. Data security needs effective storage space modern technology (https://www.vingle.net/clumi0).
Report this wiki page